Ransomware activity is climbing again, with a steep increase in the number of victims and the number of groups launching attacks. A new mid-year report from Searchlight Cyber shows how quickly the threat landscape is shifting and why CISOs need to keep adjusting their defenses.
Ransomware activity at record levels
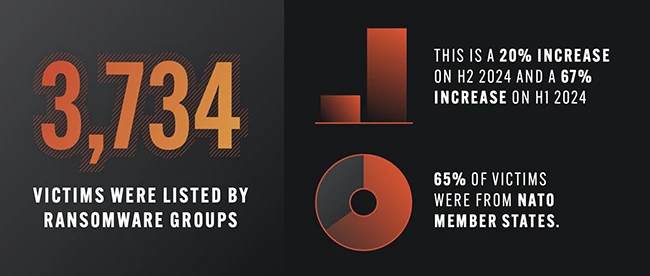
From January through June, ransomware groups listed 3,734 victims on their public extortion sites. This is a 20% increase over the last half of 2024 and a 67% jump compared to the same period last year.
The report shows that growth has been steady since early 2023, driven by the rise of the Ransomware-as-a-Service model. By letting affiliates rent ransomware tools, core groups can expand their reach without handling every attack themselves.
Most of the top five ransomware groups in the report operate under this model. This helps explain why the number of victims continues to grow even when individual groups go quiet or shut down.
More groups, more activity
The report tracked 88 active ransomware groups in the first half of 2025, up from 76 in late 2024. Of these, 35 were entirely new groups with no previous activity.
This constant turnover makes it hard for defenders to track threats. Groups often break apart, merge, or rebrand, and affiliates frequently switch from one group to another. Even when a group disappears, its members rarely leave the ransomware world for good.
The report highlights that these shifts are happening faster, which increases the complexity of defending against attacks and attributing them to specific threat actors.
Luke Donovan, Head of Threat Intelligence at Searchlight Cyber, said that this shifting landscape is also affecting the way ransomware attacks play out. “Ransomware groups have identified that the effectiveness of encrypting a victim’s content is no longer as effective as it once was. Improved backup and restoration capabilities are having an impact on the battle,” Donovan explained. “Exfiltration alone has the capability to provide significantly more damage through the pressure placed on the victim, whilst reducing the noise and time consumption of conducting the attack.”
Donovan added that while this is an evolution rather than a complete change, it reinforces the need for strong detection capabilities. “The shift in how organizations deal with this changing ransomware TTP has not been seismic. Double extortion ransomware attacks have always had an onus on exfiltration. Nevertheless, it does emphasize the ongoing requirement to continuously monitor for early detection of initial access, lateral movement, and the exfiltration of content.”
Where the attacks are hitting
Most of the observed activity targeted organizations in North America and Europe. Out of the total victims listed, 65% were in NATO member countries. The United States had the highest number of victims, followed by Canada, Germany, the United Kingdom, France, and Italy.
The report notes three main reasons for this concentration: high economic value, large attack surfaces created by advanced technology environments, and geopolitical motivations from state-linked groups.
Initial Access Brokers raise the stakes
The report also emphasizes the role of Initial Access Brokers (IABs), who sell network access on underground forums. This allows ransomware groups to bypass the time and effort required to gain initial entry on their own.
Donovan provided a real-world example of how these sales can foreshadow attacks. “In February, an initial access broker posted onto a hacking forum access to an organization named Alcott HR Group. As is typical with such posts, the broker did not name the victim but provided a description suitable to determine who the access was for. Eighteen days later, the Play ransomware group posted onto their extortion site the victim identified in the hacking forum post,” Donovan said.
“With proactive monitoring it may have been possible to have picked up the post, an investigation could have been conducted, and security measures implemented, thus reducing the likelihood of a ransomware attack or any unauthorized access from occurring.”
Donovan noted that not every brokered access sale leads to a ransomware attack, but monitoring these forums gives security teams valuable early warning. “Intelligence on initial access broker activity enables indicators and warnings to be identified. This helps pre-empt, detect, or disrupt threat actors earlier, breaking the cyber kill chain as early as possible and reducing the likelihood of the threat actor achieving their objective.”
Exploiting vulnerabilities
Many of the most active ransomware groups continue to rely on unpatched vulnerabilities to gain initial access to target networks. The report lists several major vulnerabilities exploited this year, including those affecting popular enterprise software and network devices.
These vulnerabilities are often leveraged quickly, sometimes before patches are released. That speed puts extra pressure on security teams to identify exposed systems and patch them as fast as possible.

