Instead of going after software flaws or network weaknesses, attackers are targeting something much easier to steal: identity credentials. A new report from BeyondID calls this growing black market the identity economy, where usernames, passwords, tokens, and access rights are bought and sold much like items on a regular online marketplace.
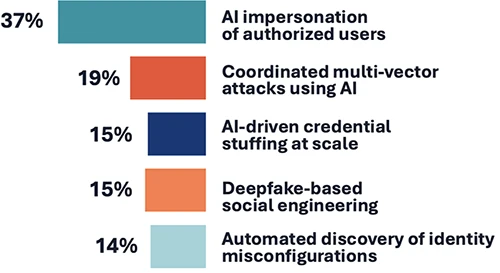
What do you believe will be the most significant AI-related identity security challenge in the next 12-18 months? (Source: BeyondID)
For attackers, stolen credentials are a shortcut. They can skip firewalls and other defenses and go straight into corporate systems. This makes them the currency of choice in the cybercrime world and has created an underground market that is hard to shut down.
The rising value of stolen access
Financial services and healthcare companies remain prime targets, but no industry is safe. A 2023 study found that 95% of enterprises experienced some form of identity fraud, with banks losing an average of $310,000 per incident.
The payouts can be massive. In February 2025, hackers tied to North Korea stole about $1.5 billion in virtual assets from a cryptocurrency exchange. Not every breach is that big, but even one compromised account can lead to stolen data, disrupted operations, and costly recovery efforts.
With quantum computing on the horizon, the value of stolen credentials will only increase. Data that is encrypted today could be decrypted later, turning old breaches into new threats.
How identity theft happens
Attackers use a mix of old and new tricks. Phishing remains one of the most common tactics, now supercharged by AI that makes fake messages more convincing. Man-in-the-middle attacks, session hijacking, and social engineering continue to be major threats.
Some attacks target human behavior rather than technology. Hackers may flood a user with MFA prompts until the person gives up and approves access out of frustration. This tactic, known as MFA fatigue, is becoming more common.
Insiders also play a role. The report found that about 60% of stolen credentials can be traced back to internal users, often through mistakes rather than intentional wrongdoing.
Technical gaps make things worse. Unused accounts, weak mobile security, and overly broad permissions give attackers more ways in. Even well-meaning companies can expose data by misconfiguring systems or poorly integrating third-party services.
Arun Shrestha, CEO of BeyondID, said many organizations are also struggling to secure the growing number of AI-driven systems. “Companies are deploying AI agents to handle core functions, but these non-human identities are often given excessive privileges or are poorly protected,” he explained. “One example involved an IT automation agent configured with superuser-level privileges, which created the potential for a region-wide infrastructure failure. In another case, attackers spoofed procurement bots at a financial institution to carry out fraudulent transactions.”
Shrestha said companies should use strong authentication, continuous monitoring, and real-time behavioral analysis for these AI agents. Privilege management and regular reviews are key to preventing attackers from taking over these systems.
Why identity management falls short
Despite the risks, many companies still treat identity and access management (IAM) as a lower priority. That leaves security teams playing catch-up while attackers exploit weaknesses that go unaddressed.
The report highlights what it calls identity exploit vectors, or common pathways that attackers follow once they get inside a system. These weak points often involve poorly protected human or machine identities, including those tied to AI agents.
Shrestha said connecting IAM goals to business outcomes is critical to fixing the problem. He shared an example of a Fortune 1000 financial services company where the IAM leader got executive support by showing the impact of better identity controls.
“Board metrics like user provisioning time, authentication success rates, and access violations helped executives see the direct value of IAM,” Shrestha said. “When the company reduced provisioning time by 45 percent and cut security incidents by 70 percent, leadership recognized IAM as a critical investment, not just a technical project.”
Steps for CISOs
CISOs can start by mapping every human and non-human identity in their environment. From there, they should enforce least privilege, remove unused accounts, and monitor activity continuously to catch suspicious behavior early.
Equally important is education. CISOs must show executives how identity theft directly affects revenue, compliance, and trust. Using metrics and business-friendly language can help secure the funding needed for stronger IAM programs.
By treating identities as valuable assets and building protections around them, organizations can disrupt the growing cybercrime economy that thrives on stolen access.

