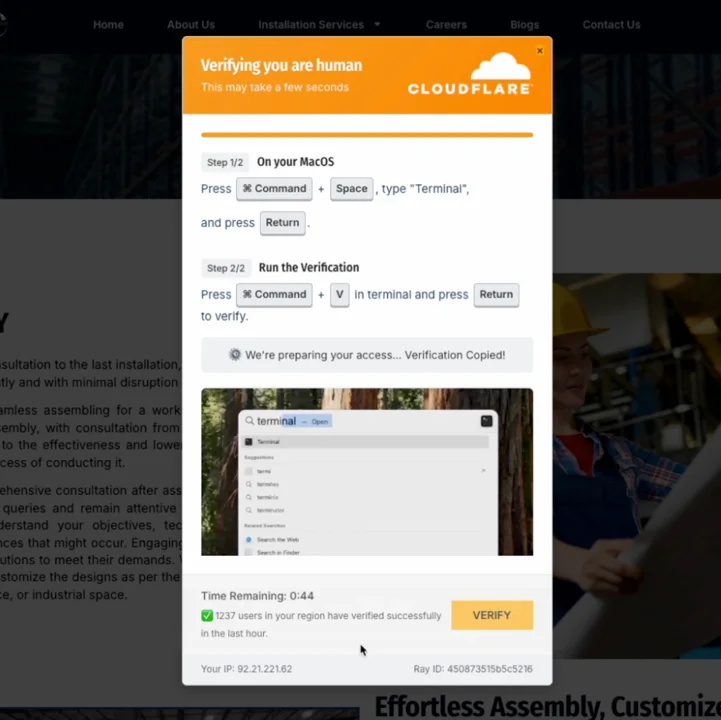
Attackers have taken the ClickFix technique further, with pages borrowing tricks from online sellers to pressure victims into performing the steps that will lead to a malware infection.
Push Security has spotted one of these pages, showing an embedded tutorial video on how to perform the asked-for actions, a timer ostensibly counting down the seconds left to act, and a “users verified in the last hour” counter – all aimed at pressing users to act quickly, without thinking.
The advanced ClickFix page (Source: Push Security)
“This is an incredibly slick example – it almost looks like Cloudflare shipped a new kind of bot check service,” the researchers noted.
To make the illusion of legitimacy complete, the page adapts to serve the correct instructions depending on the visitors’ operating system, and it’s automatically copying the malicious code to the user’s clipboard via JavaScript.
These features make the pages look credible and make the action feel normal, like completing a checkout or confirming an order. 
ClickFix’s rise
The ClickFix technique was named after the initial pretext used by the attackers: the malicious pages would show a fake error message and would instruct users to copy and run some code to fix the problem.
Malicious websites using the “click-to-fix” pretext (Source: Sekoia)
In time, the FakeCaptcha (“prove that you’re a human”) pretext became more popular, but the ClickFix name stuck, and technique became hugely popular state-sponsored threat actors.
“According to the 2025 Microsoft Digital Defense report, ClickFix was the most common initial access method in the last year, accounting for 47% of attacks,” Push Security pointed out.
Multi-channel distribution
ClickFix lures are distributed via various channels: email, instant messengers, social networks, in-app phishing, and malvertising (on search engines, YouTube, and Steam).
Malicious ads and highly-ranked pages surfaced by Google Search are currently the top delivery vector for ClickFix attacks, the researchers added.
“While other examples may have been stopped by controls such as email before the page could be loaded by the user, this shows a significant monitoring gap when it comes to non-email delivery vectors,” the company added.
Subscribe to our breaking news e-mail alert to never miss out on the latest breaches, vulnerabilities and cybersecurity threats. Subscribe here!