Researchers have introduced a new way to study and defend against ICS threats. Their project, called ICSLure, is a honeynet built to closely mimic a real industrial environment.
Why traditional honeypots fall short
Honeypots are systems designed to attract attackers so that security teams can study their behavior without putting production equipment at risk. Most ICS honeypots today are low interaction, using software to simulate devices like programmable logic controllers (PLCs).
These setups are useful for detecting basic threats but are easy for skilled attackers to identify. Once attackers realize they are interacting with a decoy, they stop revealing their tactics. That limits the data defenders can gather.
A high interaction environment
ICSLure takes a different approach. It combines actual PLC hardware with realistic simulations of physical processes, such as the movement of machinery on a factory floor. This creates what the researchers call a very high interaction environment.
For attackers, ICSLure feels like a live industrial network. For defenders, it provides more accurate data about how adversaries move inside an ICS environment and the techniques they use to disrupt operations.
Angelo Furfaro, one of the researchers behind ICSLure, told Help Net Security that deploying this type of environment safely requires careful planning. “The honeypot infrastructure must be completely segregated from any production network through dedicated VLANs, firewalls, and demilitarized zones, ensuring that malicious activity cannot spill over into critical operations,” he said. “PLCs should only interact with simulated plants or digital twins, eliminating the possibility of executing harmful commands on physical processes.”
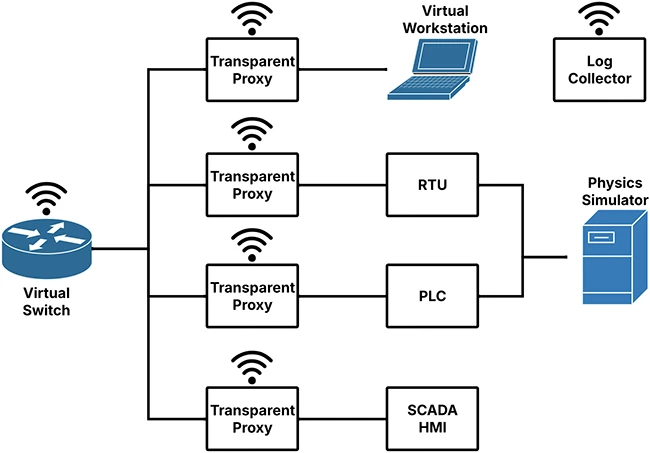
An example of the modular architecture of ICSLure
Building a convincing target
The researchers designed ICSLure as a modular system that can be customized to fit different types of facilities.
In their proof-of-concept, they modeled a wind farm. It included a Siemens PLC connected to a wind turbine simulation running in software, along with virtual workstations, routers, and a SCADA server.
To make the setup convincing, they exposed common ICS services such as Modbus and S7 and included a vulnerable engineering workstation. These elements gave attackers realistic ways to engage with the network.
Every action was logged, capturing network traffic and system changes in detail for later study.
Furfaro explained that data integrity was also a priority in their design. “All telemetry, logs, and packet captures should be cryptographically signed, timestamped, and stored in tamper-resistant repositories to ensure evidentiary value for forensic analysis,” he said. For cloud deployments, he added, encrypted channels and latency-aware orchestration are key to maintaining realism while preventing data leakage.
Capturing full attack chains
The team tested ICSLure by deploying it on a public academic network for 30 days. During that time, they collected over 2 GB of network traffic.
Most of the activity was automated scanning and fingerprinting, but the system also recorded targeted attacks that the researchers launched themselves. These included attempts to manipulate turbine controls through Modbus commands and to take over the engineering workstation.
The results showed that ICSLure can capture complete, multi-stage attacks, from initial access to physical process disruption. This capability is critical for understanding ICS malware like FrostyGoop or complex threats similar to Stuxnet.
“Incident containment mechanisms such as sandboxing, rate limiting, and automated intrusion throttling are needed to prevent attackers from exploiting ICSLure as a launching pad for further attacks,” Furfaro said. “Since the entire system is backed up to a consistent state using Ansible and Terraform, it can be quickly restored to a secure configuration after an incident, which also helps repeat experiments safely.”
What ICSLure reveals about real-world threats
ICSLure demonstrates how realistic honeynets can help defenders learn more about ICS threats. By studying how attackers interact with a believable environment, security teams can improve detection rules, refine incident response playbooks, and uncover weaknesses in network design.
Luigi Lenguito, founder and CEO of BforeAI, said ICSLure signals an important shift in how defenders approach ICS security. “ICSLure represents a step forward in bringing a more dynamic, deception and moving target based approach to modernizing detection engineering for OT networks,” he said.
Lenguito noted that OT environments are often highly customized and lack standardization, which adds complexity for attackers. “This creates a significant challenge for attackers, who must invest considerable time and resources to explore the environment and identify potential entry points,” he explained. “Deploying decoys and honeypots takes advantage of this complexity, providing an effective way to detect anomalous activity early and gain insight into potential attacks.”
He added that the next hurdle will be turning these insights into actionable intelligence. “The challenge is volume, since OT today is in many ways where IT was 15 years ago,” Lenguito said. Sharing and correlating these data points to generate intelligence and document adversary TTPs is the next big step.
Taking ICSLure beyond the proof-of-concept
The research also highlighted the danger of exposed ICS devices. During their work, the team found many vulnerable PLCs visible on the internet through basic search tools. This reinforces the need for segmentation and strict access controls.
Scaling ICSLure for larger, distributed environments will bring new challenges. “The foremost issue is synchronization across distributed components,” Furfaro said. “Maintaining real-time consistency between physical PLCs and multiple simulators over wide-area networks is non-trivial, particularly when considering clock drift, variable latency, and jitter.”
He also pointed to the difficulty of making these networks appear authentic to attackers. “Realistic propagation delays, routing behaviors, and fault conditions must be emulated convincingly without revealing the honeypot’s artificial nature,” he explained.
The researchers plan to partner with industrial organizations to test ICSLure in real-world environments. They also want to explore how it can fit within legal and regulatory frameworks. “Such collaborations and regulatory assessments will not only strengthen the practical relevance of ICSLure but also bridge the gap between experimental research and deployable, industry-grade security solutions,” Furfaro said.

